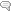Transparent Data Encryption (TDE) keeps your data files and backups encrypted. TDE protects both physical data and transaction log files. If the files are moved to another server, those can’t be opened and viewed on other server. TDE protects data at rest while data tables are not directly encrypted. This means, if a user has permission to a database with TDE enabled, that user can see all the data. TDE was first introduced in on-premise version of SQL Server 2008.
SQL Azure TDE works similarly, but the configuration of is much simpler than on-premise SQL Server. Here is how you can enable TDE:
- Go to Azure portal portal.azure.com
- Choose your database and go to settings
- Click on Data Encryption On option (Check the below screenshot)
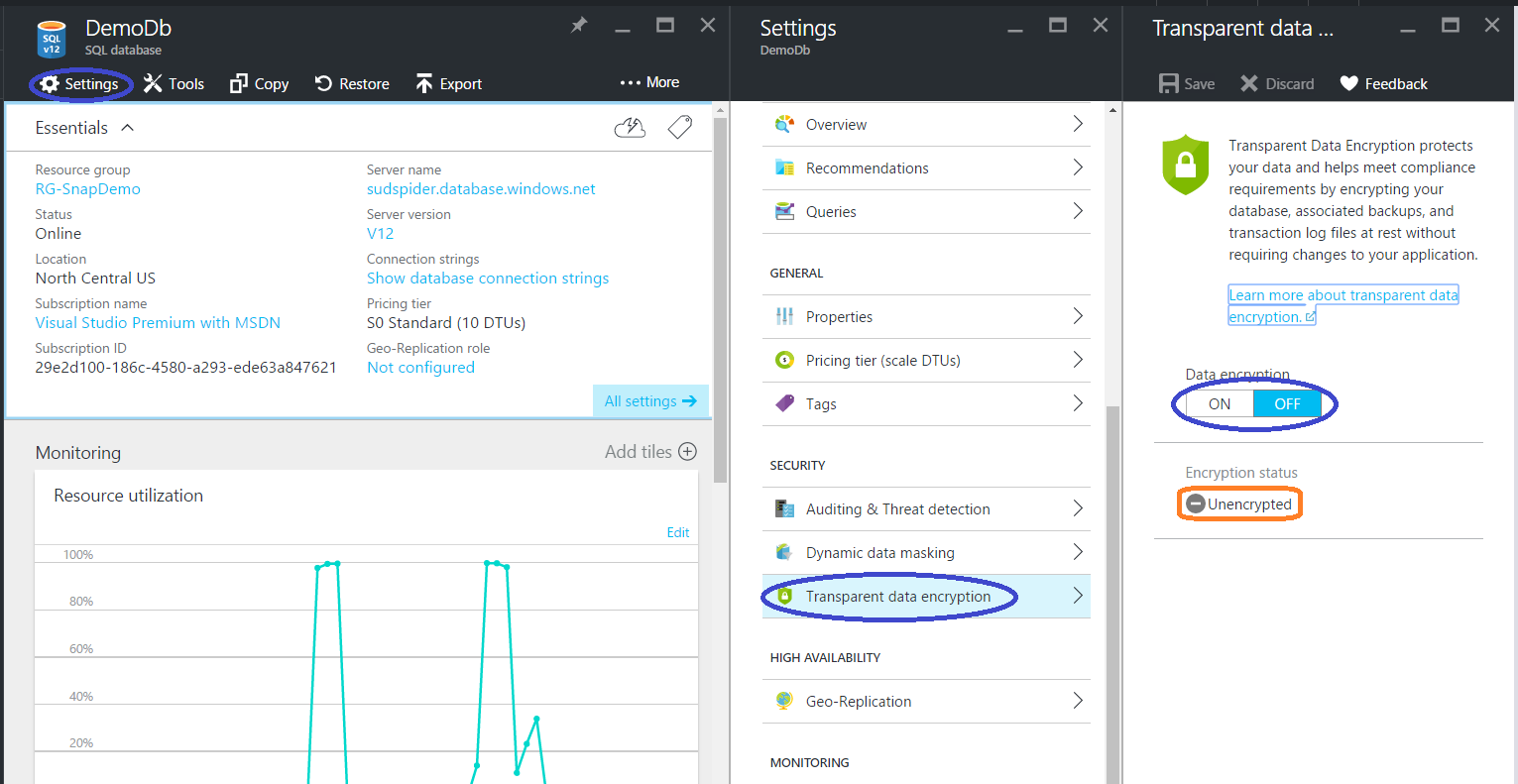
Change the Data Encryption value to ON and Save (at the top right hand corner of the page). Check for the ‘Encryption Status’’, after a while it will say Encrypted.
TDE in SQL Azure is implemented on top of the same data transparency feature running since SQL Server 2008. Some enhancements are made to the core technology to reduce the CPU overhead caused by turning on TDE.
Few important things to note about TDE feature in SQL Azure:
- There are NO CHANGES required in the application
- It encrypts database using symmetric key, also called as database encryption key
- Database encryption key is protected by built-in server certificate which is unique for each SQL Azure Database Server
- If there are multiple databases on same server then same certificate shared by them
- Built-in certificates will be changed by Microsoft after every 90 days for security purposes
- If you have enabled Geo Replication on the database, then it is protected by different keys on different servers
- SQL Azure does not support Azure Vault integration with TDE
If you want to implement stronger security than encrypting data at rest (TDE) then please read this article “Always Encrypted”.